Google Ads Performance Max Replaces Smart Shopping & Local Campaigns
Performance Max or Google PMax is set to replace Smart Shopping and Local campaigns in 2022….
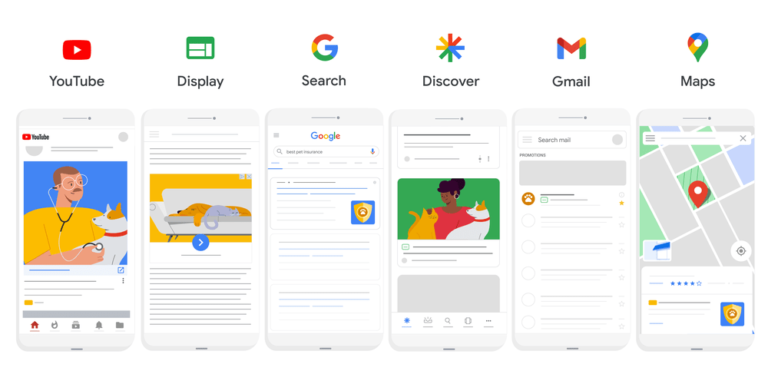
Performance Max or Google PMax is set to replace Smart Shopping and Local campaigns in 2022….
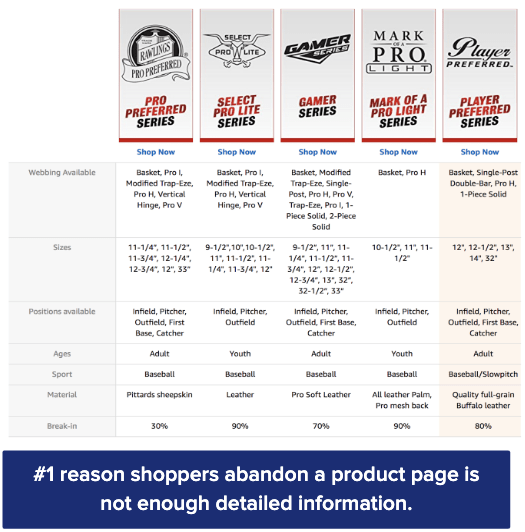
It’s never been more important to stand out on the digital shelf. Enhanced content empowers you…
Competition is core to the free market concept. By finding ways to outpace, outperform, and outproduce…

Last Updated on February 14, 2022 Performance Max campaigns are taking the world of Google Ads…

Your Instagram ads have the potential to reach 840+ million potential shoppers. Is your Instagram marketing…
Brick-and-mortar stores used to be the primary focus for driving sales. Prime product placement on a…
When you’re running a small business, you want to take advantage of every marketing tactic available….
Shopping is now an omnichannel, nonlinear journey across the digital shelf. In an effort to understand…

Online food and drink sales have skyrocketed in the last few years and are poised for…

If you’re an ecommerce professional, you likely know the importance of personalization. Basic elements of personalization,…